3 Reasons to Leverage Snowflake to Build HIPAA-compliant Data Infrastructure
TL'DR
What is HIPAA and its purpose?
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal law that requires the creation of national standards to protect sensitive Patient Health Information (PHI) from being disclosed without the patient’s consent or knowledge.
How to become HIPAA compliant
1. Create Privacy and Security Policies for the Organization
Becoming HIPAA compliant requires more than simply following HIPAA Security and Privacy Rules. Covered entities and business associates must also prove that they’ve been proactive about preventing HIPAA violations by creating privacy and security policies.
These policies must be documented, communicated to staff, and regularly updated. In addition, staff must be trained on HIPAA policies during orientation and at least once a year. Finally, they must attest (in writing) that they understand all HIPAA policies and procedures.
2. Name a HIPAA Privacy Officer and Security Officer
HIPAA legislation is complicated and ever-changing, so every organization needs its own internal HIPAA experts.
The HIPAA Security Rule requires covered entities to designate a Privacy Compliance Officer to oversee the development of privacy policies, ensure those policies are implemented, and update them annually. In addition, the Privacy Officer and Oversight Committee members must undergo regular training to stay abreast of changes to HIPAA regulations.
Covered entities are also required to have a HIPAA Security Officer to ensure policies and procedures are in place to prevent, detect, and respond to ePHI data breaches. The Security Officer establishes safeguards required by the Security Rule and conducts risk assessments to gauge their effectiveness.
3. Implement Security Safeguards
The Security Rule requires three types of safeguards that covered entities and business associates must have in place to secure ePHI - including:
- Administrative Safeguards: Organizations must document security management processes, designate security personnel, adopt an information access management system, provide workforce security training, and periodically assess security protocols.
- Physical Safeguards: Organizations must control who has access to physical facilities where ePHI is stored. They must also secure all workstations and devices that hold or transmit ePHI.
- Technical Safeguards: Organizations must have access controls to secure ePHI in the EHR and other databases to ensure employees only see data they’re authorized to visit. Data must be encrypted at rest and during transit, which creates the need for secure email, HIPAA Compliant Texting, and HIPAA Compliant Messaging solutions. Organizations must also have audit controls for all hardware and software that manage or transmit ePHI to ensure they meet HIPAA network requirements. And there must be integrity controls to ensure ePHI is not improperly edited or deleted.
4. Regularly Conduct Risk Assessments and Self-Audits
Becoming HIPAA compliant is not a do-once-and-done process. Covered entities and business associates have to conduct regular (at least annual) audits of all administrative, technical, and physical safeguards to identify compliance gaps. Organizations must then create written remediation plans that clearly explain how they plan to reverse HIPAA violations and when this will happen.
5. Maintain Business Associate Agreements
Before sharing PHI with business associates, covered entities must obtain “satisfactory assurances” that the business associate is HIPAA-compliant and can effectively safeguard the data. In addition, the parties must enter a BAA. All BAAs must be reviewed annually and updated to reflect any changes like the business associate relationship.
6. Establish a Breach Notification Protocol
A HIPAA violation doesn’t always get organizations into trouble, especially if they can prove the breach was unintentional and that they did everything in their power to prevent such breaches. But failing to report violations makes the situation worse.
The HIPAA Breach Notification Rule requires covered entities and business associates to report all breaches to the Office for Civil Rights (OCR) and notify patients whose personal data might have been compromised. In addition, HIPAA-beholden organizations must have a documented breach notification process that outlines how the organization will comply with this rule.
7. Document Everything
Organizations must document all HIPAA compliance efforts — including privacy and security policies, risk assessments and self-audits, remediation plans, and staff training sessions. OCR will review all this documentation during HIPAA audits and complaint investigations.
HIPAA compliance is critical for healthcare organizations, not only to protect patient privacy but also to protect the bottom line. To keep data safe, healthcare providers need to know how to become HIPAA compliant, and they need technology partners who take it just as seriously as they do.
The three components of HIPAA security rule compliance
- Administrative Controls: Ensure that patient data is correct and accessible to authorized parties. Formalize your privacy procedures in a written document.
- Physical Security: Help your organization prevent physical theft and loss of devices that contain patient information.
- Technical Security: Protect your networks and devices from data breaches.
How could you leverage Snowflake?
The below diagram lists out how Snowflake makes sure it covers the above three components of HIPAA.
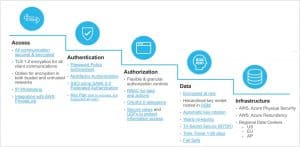
Administrative
Account/user authentication
- Key Pair Authentication & Key Pair Rotation for increased security with client authentication
- MFA (multi-factor authentication) for increased security for account access by users
- OAuth for authorized account access without sharing or storing user login credentials
- Support for user SSO (single sign-on) through federated authentication.
Access Control
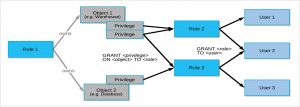
In the Snowflake model, access to securable objects is allowed via privileges assigned to roles, which are assigned to other roles or users. In addition, each securable object has an owner that can grant access to other roles. This model is different from a user-based access control model, in which rights and privileges are assigned to each user or group of users. The Snowflake model is designed to provide a significant amount of both control and flexibility.
Data Encryption
Protecting customer data is one of Snowflake’s highest priorities. Snowflake encrypts all customer data by default, using the latest security standards, at no additional cost. In addition, Snowflake provides best-in-class key management, which is entirely transparent to customers. This makes Snowflake one of the easiest-to-use and most secure data platforms available.
Physical security
Snowflake is hosted on cloud services like AWS and Azure, heavily protected and guarded against natural and manmade calamities. Refer below link for AWS and Azure Controls on its data centers:
- https://aws.amazon.com/compliance/data-center/controls/
- https://learn.microsoft.com/en-us/azure/security/fundamentals/physical-security
Technical security
Protect your networks and devices from data breaches.
End-to-End Encryption
End-to-end encryption (E2EE) is a form of communication in which no one but end users can read the data.
In Snowflake, this means that only a customer and the runtime components can read the data. No third parties, including Snowflake’s cloud computing platform or any ISP, can see data in the clear.
E2EE minimizes the attack surface. For example, in the event of a security breach of the cloud platform, the data is protected because it is always encrypted, regardless of whether the breach exposes access credentials indirectly or data files directly, whether by an internal or external attacker.
Network/site access
- Site access is controlled through IP allow and block lists, managed through network policies.
- AWS PrivateLink and Azure Private Link are used to accomplish private connectivity to the Snowflake service. (Business Critical Edition or higher).
- Private connectivity to Snowflake internal stages is done using Azure Private Link. (Business Critical Edition or higher).
Are you looking for certified Snowflake Engineers? Or experts to setup HIPAA compliant Data Infrastructure? Click here to get in touch with our experts.









%20AI%20in%20Data%20Quality_%20Cleansing%2C%20Anomaly%20Detection%20%26%20Lineage.avif)















